1. Why Kubernetes‑Native Matters
Over the years, Kubernetes has evolved from container orchestration to becoming the foundation for a resilient infrastructure framework. Its design around desired‑state reconciliation, automated restarts, and scaling makes it ideal for systems that need to be fault‑tolerant and cloud‑agnostic.
2. Embrace Multi‑Cloud Resilience
Operating across AWS, GCP, Azure—or even on‑prem/data‑center environments—not only helps avoid vendor lock‑in, it builds redundancy and global scale.
Key best practices include:
-
Deploying multiple clusters via tools like Rancher, OpenShift, or GitOps (ArgoCD, Flux)
-
Replicating data cross-cloud using Velero, CockroachDB, or Spanner
-
Using global load balancers and traffic routing to shift traffic during outages
3. Kubernetes Federation + Service Mesh
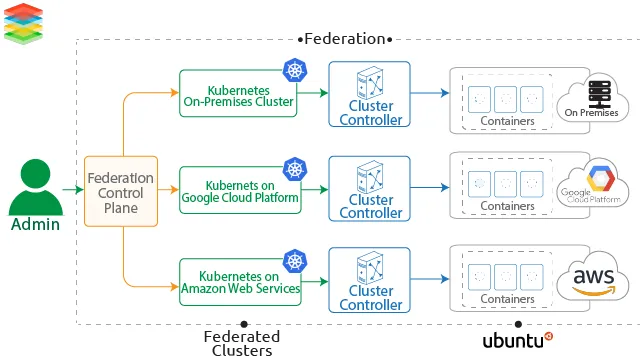
Federation allows unified control across several Kubernetes clusters. If one fails, workloads and traffic flow shift to healthy regions automatically.
A service mesh (Istio, Linkerd, or Cilium mesh) ensures secure, observable inter-service communication—offering retries, circuit-breaking, and mTLS consistently across clusters
4. Self‑Healing at Every Level
Kubernetes already restarts failed pods, replaces unresponsive nodes, and keeps resources aligned with declared state
But production systems require more:
-
Self‑Healing Frameworks: Real-world platforms add automated detectors and fixers for cloud-level issues (e.g. Azure glitches)
-
AI‑Driven Healing: Cutting‑edge setups use ML to predict failures—memory leaks or anomalies—and proactively restart pods or reschedule traffic
-
Graceful Degradation: Systems can shut down lower‑priority containers to preserve critical services during resource crunch
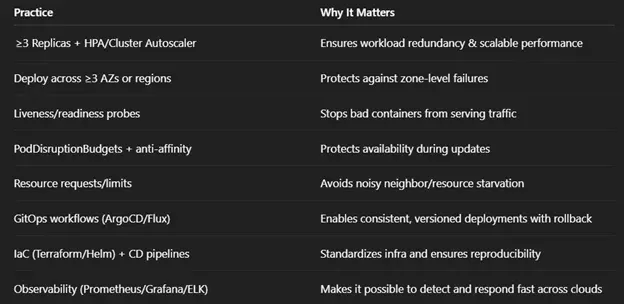
5. Foundations of Resilience: Kubernetes Best Practices
6. Disaster Recovery & DR Strategy
Planning for cloud/provider-level failures includes:
-
Regular backups (etcd, PVs, databases) via Velero/S3 cross-region replication
-
Latency-based routing (Route 53 or cloud LB) between active-active or active-passive clusters
-
CI/CD pipeline redundancy—keep secondary GitOps/WF cluster always in sync
-
Secure secrets vault replication (Vault, sealed-secrets)







