Cyber attackers are actively targeting Palo Alto Networks PAN-OS firewalls by exploiting a recently patched authentication bypass vulnerability, tracked as CVE-2025-0108.
This high-severity flaw impacts the PAN-OS management web interface, allowing unauthenticated attackers with network access to bypass authentication and execute specific PHP scripts. The exploitation could lead to compromised system integrity and confidentiality.
Urgent Security Advisory
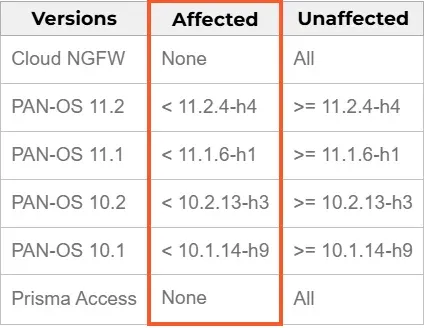
In a security bulletin released on February 12, 2025, Palo Alto Networks strongly advised administrators to upgrade their firewalls to the following patched versions:
-
11.2.4-h4 or later
-
11.1.6-h1 or later
-
10.2.13-h3 or later
-
10.1.14-h9 or later
Additionally, PAN-OS 11.0, which is also vulnerable, has reached end-of-life (EoL) and will not receive a security patch. Users running this version are urged to upgrade to a supported release to mitigate potential risks.
Vulnerability Exploitation and Attack Methods
The vulnerability was first discovered and reported by security researchers at Assetnote, who later published a detailed analysis upon the patch's release. Their research demonstrates how attackers can exploit the flaw to:
-
Extract sensitive system data
-
Retrieve firewall configurations
-
Manipulate certain settings within PAN-OS
The attack leverages a path confusion issue between Nginx and Apache within PAN-OS, which allows authentication bypass. Threat actors with network access to the management interface can exploit this weakness to gather intelligence for further attacks or weaken security defenses by modifying system settings.
Active Exploitation in the Wild
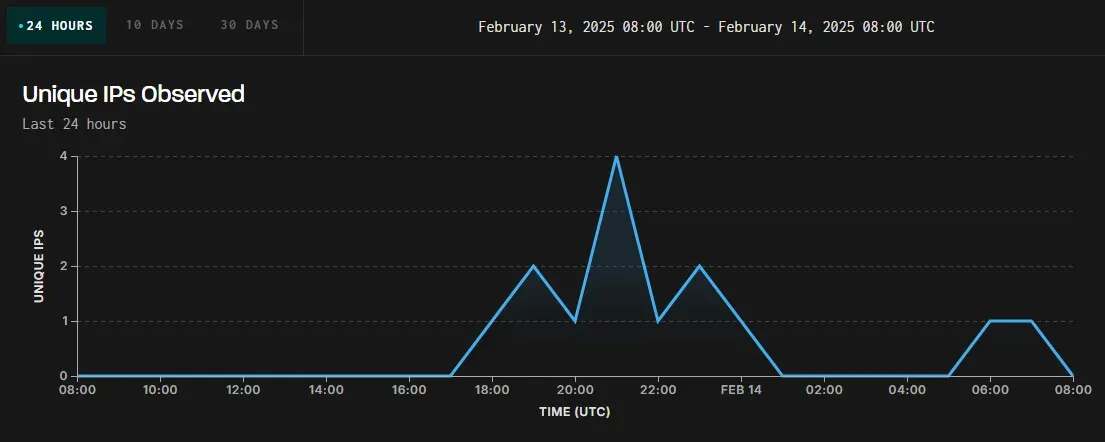
Security monitoring service GreyNoise has detected ongoing attacks attempting to exploit unpatched PAN-OS firewalls. Exploitation attempts were first observed on February 13, 2025, at 17:00 UTC, originating from multiple IP addresses, indicating that different threat actors may be involved in these efforts.
Research from Macnica security expert Yutaka Sejiyama reveals that over 4,400 PAN-OS devices are currently exposing their management interface online, making them prime targets for cybercriminals.
Mitigation Measures and Recommendations
Given the public availability of proof-of-concept (PoC) exploits, the likelihood of continued and escalating attacks remains high. To protect against these threats, organizations are urged to take the following actions:
-
Apply the latest security patches immediately.
-
Restrict access to firewall management interfaces to minimize exposure.
-
Follow best practices for securing external-facing management interfaces to reduce the risk of unauthorized access.
Palo Alto Networks' Official Response
On February 18, 2025, Palo Alto Networks issued a statement confirming active exploitation of CVE-2025-0108 and warning that attackers are chaining it with other vulnerabilities, such as CVE-2024-9474, to gain unauthorized access to unpatched firewalls.
"The security of our customers is our top priority. We have confirmed reports of active exploitation targeting CVE-2025-0108. Organizations with internet-facing PAN-OS management interfaces must apply the security updates released on February 12, 2025, as soon as possible. Securing external-facing management interfaces is a fundamental security best practice, and we strongly encourage all organizations to review their configurations to minimize risk."
For detailed information and mitigation guidance, users should refer to the official security advisory: CVE-2025-0108 Security Advisory.
As cyber threats continue to evolve, maintaining up-to-date security patches and following best practices for system protection remain crucial in defending against such exploits.







